
It’s what enables web browsers and servers to share information, including web pages and media files. This setting forces all website connections to use the secure HTTPS protocol rather than HTTP, an insecure version that leaves you vulnerable to eavesdropping. By default, Tor has stricter privacy settings than most standard web browsers. Users can take further steps to maximize privacy when browsing with Tor.
Accessing The Dark Web With Tor Browser And VPN
Do not use any personally identifiable information on the dark web. Use aliases and avoid any activity that might reveal your identity. By following these steps, you’ll have I2P and Hyphanet set up for secure and private browsing on the dark web. Both networks have unique strengths, and while they aren’t as user-friendly as Tor, they offer excellent alternatives for those seeking robust privacy and decentralized communication options. For more advanced use, Hyphanet allows you to create and host your own freesites, participate in forums, and communicate anonymously with other users.
- JavaScript has been used to exploit Tor in the past, which makes Windows users particularly vulnerable.
- Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet.
- Virtually anything you can buy on the surface or clear web you can also find on the dark web.
- However, navigating this hidden digital landscape in 2025 presents heightened security risks, from advanced cyber threats to targeted surveillance.
- With its reputation for hosting illegal content, many wonder about the legality of accessing this hidden part of the internet.
- As mentioned earlier, many websites consider Tor suspicious and block users entirely.
Tips To Stay Safe When Using The Dark Web
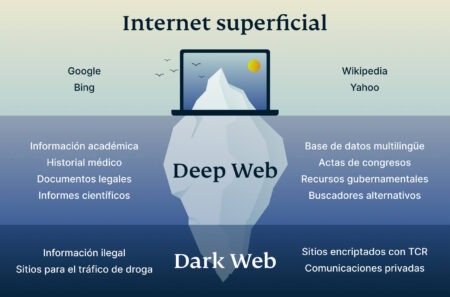
Its foundation is the Onion Router (Tor) project, developed in the 1990s with funding from the U.S. Naval Research Laboratory to protect sensitive government communications. Later released as open-source, Tor became accessible to the public, enabling anonymous browsing for activists, journalists, and everyday users—while also giving rise to today’s dark web. The dark web isn’t only about illegal activities; its primary purpose is to provide maximum anonymity by making your connection private online through encrypted servers. While the dark web is famously known as an illegal platform for criminal activities, that’s not all about this part of the web.
How To Set Up And Use Tor For The First Time
However, HTTP on its own isn’t secure– it doesn’t encrypt data during transmission, which leaves an opening for third parties to spy on your online activities. Tor doesn’t support plugins because they introduce security risks. Malicious actors often target browser plugins to steal website credentials or install malware on unsuspecting devices, so Tor sidesteps these risks altogether. However, the most secure way to use Tor is via .onion sites, which are built exclusively for the Tor network. With this setup, you connect to your VPN first, then open Tor Browser.
In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.
Do I Need A VPN To Access The Dark Web Using Tor?
There’s evidence that law enforcement agencies in freer countries operate many exit nodes for monitoring and surveillance purposes. This is because Tor traffic is usually unencrypted when it passes through the exit node. The dark web frequently plays host to fraudulent activities, including bogus offerings and schemes designed to deceivefully acquire users’ funds and sensitive data. There exists a considerable danger of identity theft, underlining the importance of utilizing tools that monitor the dark web to ensure the protection of personal information. When exploring this hidden part of the internet, adhering to safe browsing habits is crucial. This includes steering clear of illegal activities and vigilantly safeguarding one’s personal information to avoid any unwarranted exposure or threats.
This type of government surveillance applies mostly to countries with environments that are hostile to free speech. You can either sell or buy goods on the dark web, but both present difficulties. The dark web is also a place for scammers to attract vulnerable and unwitting victims. The platform is also used by governmental cyber departments to identify and track potential criminals or offenders.
How To Download WinRAR For Extracting Files For 64/32 Bit Versions 2024

It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Initially, the dark web was mainly used by government agencies, big businesses, hackers, and cybercriminals.

Commercial Services

It hosted over 7,000 .onion categorized links to make surfing the web easier. One of Daniel’s impressive features was the built-in functionality that showed whether a particular dark website is online. After more than a year of no updates, the site admin shut it down, reasoning that he couldn’t keep the list of onion links up-to-date. Since Tor has to pass your traffic through several nodes, it will slightly slow your speeds.
Accessing Hidden Services
Absolutely no one knows who’s surfing on the dark web, who is selling, who is buying or anything like that – as long as you take the correct safety and online privacy precautions. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. If your Social Security number is found on the dark web, take immediate action to protect yourself.

China has outlawed the anonymity service and blocks Tor traffic from crossing the Great Firewall. Countries such as Russia, Saudi Arabia, and Iran are working hard to prevent citizens from using Tor. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities.
Dark Web Search Engines
While there are numerous VPN services that work well with Tor, I’ve found that NordVPN offers the best protection and compatibility, and keeps your personal information safe. This is why I strongly suggest using a Virtual Private Network to protect and enhance all of your online activities. A VPN keeps all of your online activities – including your web browsing, online gaming, streaming, and file-sharing – undercover and safe from being tracked or recorded. Another reason you don’t want to use the Tor Browser for your daily web browsing is that it draws attention to you. The Tor Browser prevents your ISP from seeing what websites you’re visiting, but it does not prevent the ISP from seeing that you’re using Tor.
Law enforcers can use custom software to infiltrate the dark web and analyze activities. You could be monitored closely even if you are not doing anything illegal. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows.
The dark web is a decentralized web, which means that the data is stored on many different servers around the world. It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes. Those who access the dark web do so via the Tor (The Onion Router) browser.



