Here, you’ll find threads and detailed discussions on Socks, cardable websites, anonymity, VPNs, operating systems, hacked accounts, databases etc. NFC (Near Field Communication) fraud is a growing concern due to the increasing adoption of NFC technology in mobile payments, identity verification, and other contactless applications. The rise of contactless payments, especially during the COVID-19 pandemic, has significantly increased the volume of NFC transactions. This growth has created more opportunities for fraudsters to exploit the technology.
- They may obtain this information through hacking, social engineering, or by purchasing it from other hackers.
- These services act as intermediaries between the user and the target website, routing internet traffic through different IP addresses and servers.
- Unlike a credit card, a debit card is connected directly to your checking account, allowing fraudsters to immediately drain your account.
- Skimming involves attaching hidden devices to card readers, such as ATMs or gas station pumps, to capture card data directly from the magnetic stripe as customers perform legitimate transactions.
- Fraudulent actors would steal wallets or purses to gain access to credit cards, or place devices on ATMs or POS terminals that captured card information during swipes.
In today’s digital era, where information is constantly on the move across all digital platforms, an… Moreover, it’s essential to provide the company staff with enough training as well as defined objectives of what they should look for to bolster the monitoring efforts. Perhaps that’s their option for generating consistent traffic and a steady influx of new members. Perhaps its strong community is helping the administrators to keep the forum alive after all the attempts by authorities to seize. While authorities have failed to shut it down, the forum hasn’t, fortunately, witnessed easy sailing either. For instance, in January this year, it was the target of Operation Talent, the law enforcement initiative that was coordinated by the FBI and international agencies.
Staying Safe Online

Its structured organization and membership policies project professionalism, attracting genuine content and marginalizing non-Russian speakers. LeakBase, launched in January 2023, quickly filled the void left by BreachForums. This English-speaking forum, accessible on the surface web, gained nearly 50,000 members swiftly. It discusses data leaks, vulnerabilities, malware, and legal tools, attracting prominent threat actors.
If you think your site has been carded, look for a spike in small transactions or failed payment attempts, multiple payments from the same IP or device, or increased chargebacks and fraud complaints. Protecting your platform from carding isn’t just about installing a firewall; it’s about making a system that deters fraud at every stage. As ever, always be careful when entering your account details online, and of course, get in touch with your bank if you do see any suspicions transactions. Bahira has generated buzz in both Russian and English-speaking dark web spaces and boasts the sale of both card details and dumps (the information encoded onto a card’s magnetic stripe and used to make physical clones). You may have never been to the dark web — but there’s a chance your credit card information has. An increase in cybercrime-related arrests and site takedowns by Russian authorities have been observed recently, beginning with the arrest of 14 members belonging to the REvil ransomware group in mid January.
Top 10 Deep Web And Dark Web Forums
Withoutdecisive action, these cybercriminals will continue to exploit NFCtechnology, posing a serious risk to consumers and businessesworldwide. The threat actor’s marketing strategy involves leaking a large number of credit cards to attract potential clients from hacking and cybercrime forums. This move is likely to increase the platform’s popularity and draw in new customers. The ease of access and navigation of Telegram carding groups is a major concern, as it allows cybercriminals to easily buy and sell compromised payment card details. Free and paid tutorials on the dark web teach fledgling criminals how to use stolen credit cards. Forums are a source of credit card data for carding, and can also be used to share the results of carding – for example to sell success credit cards to other criminals.

How Are Credit Card Data Stolen?
This is for operators who understand that sourcing quality product is the single most important link in the chain. The shutdowns have led to discussions about operational security, as some forum members fear they could also be arrested. “Hard times have come. Take care of yourself and remember your safety,” said one user.

Apple Watch Ultra 3 Review: Biggest Is Best, Except If It’s Not
B1ack’s Stash’s sudden rise in popularity has been met with mixed reactions from dark web users. Most comments range from negative to neutral, while very few users gave clearly positive endorsements based on their site experience. Abraham Lebsack is a seasoned writer with a keen interest in finance and insurance. Credit card prices also vary depending on the brand, with American Express being worth the most at 5.13 cents per dollar. The resulting financial loss from stolen information is tremendous, not only for the individual victim but also for the financial provider and any involved organizations.
BidenCash Darkweb Market Gives 19 Million Credit Cards For Free
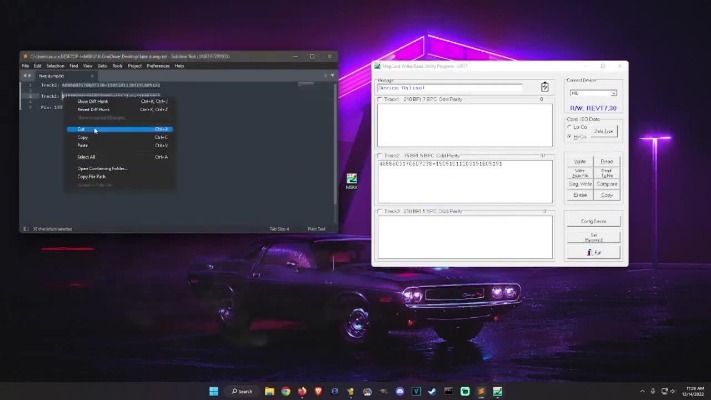
It literally has topics such as “carding discussions”, “programming”, “anonymity and security”, “hacked databases”, “hacking/cracking tutorials” etc. However, in terms of registered users and active threads about carding it’s definitely one of the best. Typically,these merchants have a daily limit, so cybercriminals are alwayslooking for new ways to scale their operations by adding new moneymules who can open accounts for a commission. TheZ-NFC behaves like a malware loader, using advanced Android packing,native code injection, and NFC emulation to conceal and executepayloads. The ability to emulate NFC cards dynamicallymay enable physical security bypass or unauthorized access inreal-world environments.
Ready To Explore Web Data At Scale?
BreachForums made its name as one of the top forums for leaked databases as well as stolen credentials immediately after RaidForums was closed down. It’s a well-known forum for strong escrow services, a repository of more than 15 billion records, and a VIP ranking system that makes it a top player. The fact that it discusses vulnerabilities, legal tools, data leaks, and malware attracts prominent threat actors constantly.
The Chinese government and theChinese Communist Party (CCP) have been accused of supporting cyberoperations that target foreign governments, businesses, andindividuals. Additionally, China has accused other nations, suchas the United States, of engaging in cyberattacks, furthercomplicating the issue. The threat actor behind the AllWorld Cards marketplace has a clear goal in mind.
Anthropic Touts Safety, Security Improvements In Claude Sonnet 45
The victims of carding may suffer significant financial losses, damage to their credit scores, and emotional distress. Moreover, the profits made from carding often fund other criminal activities, such as drug trafficking or human exploitation. Elliptic’s internal research team continues to actively monitor illicit activity on the dark web and label newly identified illicit services in its tools.
Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. The shop offers stolen card data from around the world for as low as $0.15 per item and uses verification and automated checks to check the validity of the cards people put up for sale on the platform. The data posted on these online illicit shops is a goldmine for threat actors who are looking to commit financial crimes.
It’s not a “marketplace” as it has discussion topics on RDPs, VPNs, Socks, list of cardable sites etc. It even has a marketplace section where users can buy/sell cards, malware, hacking tools etc. Additionally, a “Service” section exists where you can find users willing to do your bid given enough incentive.
I agree to Money’s Terms of Use and Privacy Notice and consent to the processing of my personal information. “The most important thing is for people to keep an eye on their transactions and report any fraud immediately,” Krebs says. The UniCC team also gave its users 10 days to spend their balances, while also warning customers to “not follow any fakes tied to our comeback.” Watch our cyber team share their key insights from their investigations into the biggest dark web trends in 2022.

Since 2020, 2easy has sold massive stealer logs with sensitive data like passwords, bank cards, and initial access credentials. It supports operations in multiple languages and operates on both clearnet and Tor. Trump’s Dumps was another prominent carding site specializing in selling raw magnetic strip data from compromised cards – commonly referred to as “dumps” by carders. It made around $4.1 million since its establishment in October 2017 according to Elliptic’s internal data.



